2
Lessons
2
Videos
Intermediate
Skill Level
00:30h
Duration
English
Language
Overview
This course will introduce you to our analysis and remediation solutions. There are many ways in which you can use SafeBreach platform to analyze your security posture and receive helpful remediation ideas that you can implement or activate using your existing security controls.
In this course, you will learn :
> Simulation results analysis tools
> Remediation methods via 3rd-party software, using policies and rules
Lesson 1 -
Analysis Options
After running various attack scenarios at different times, you will have enough telemetry to analyze. There are many ways you can analyze your attack data, and you need to choose your preferred methods according to your points of interest.
Let’s learn about some of the analysis options:
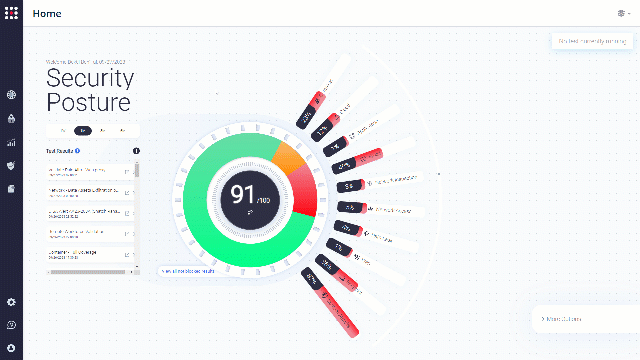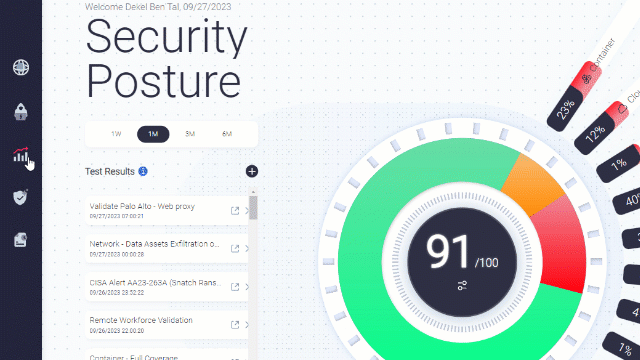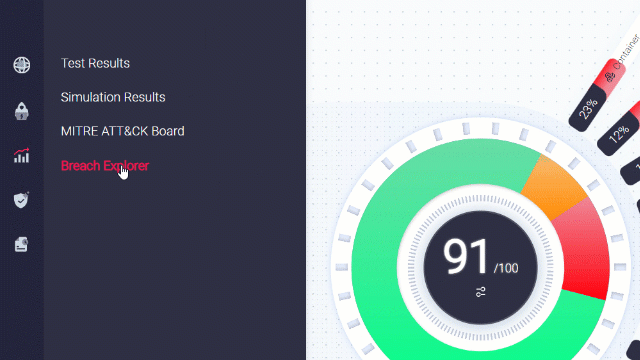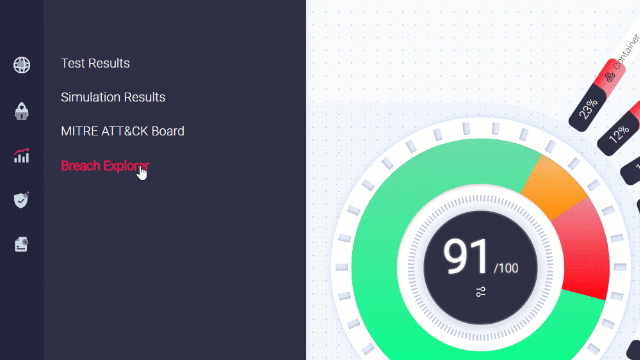
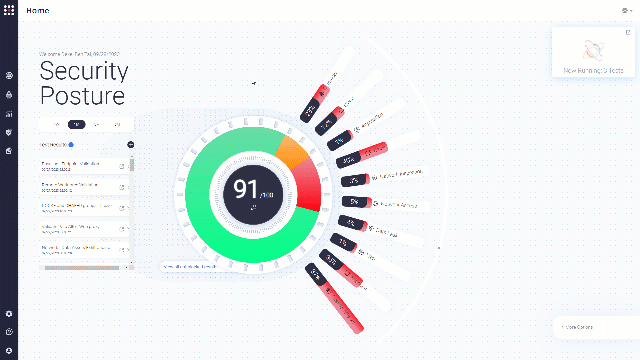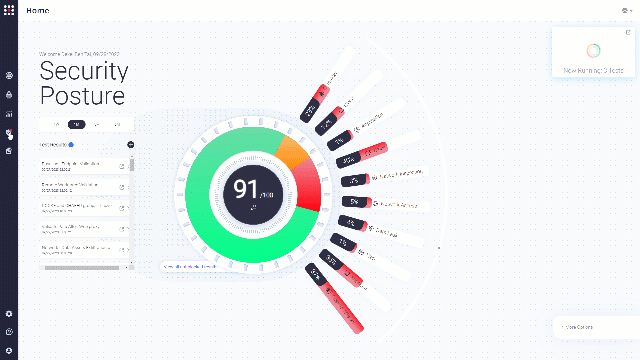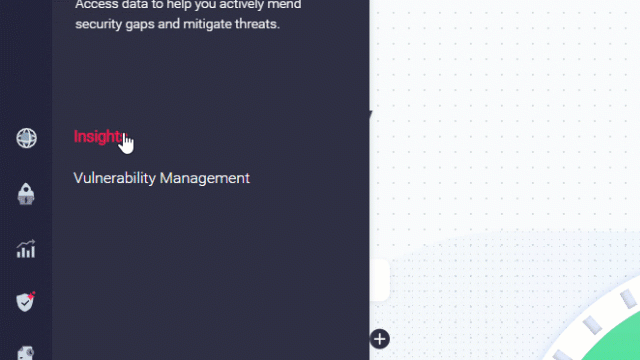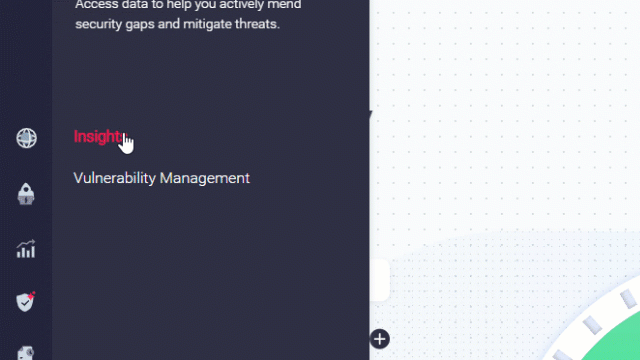
Security Posture Analysis
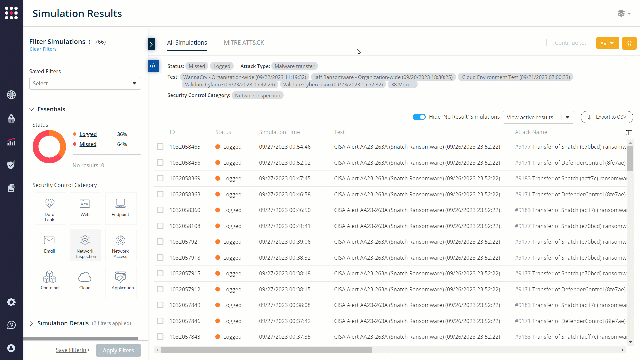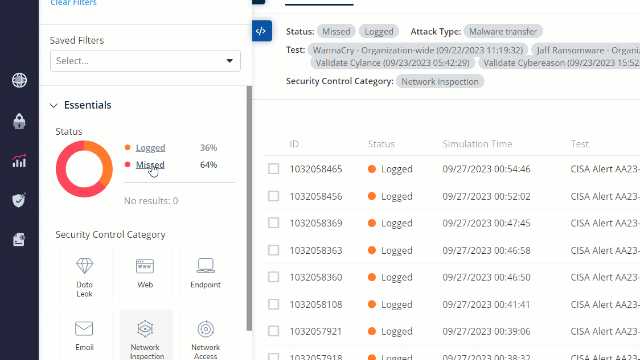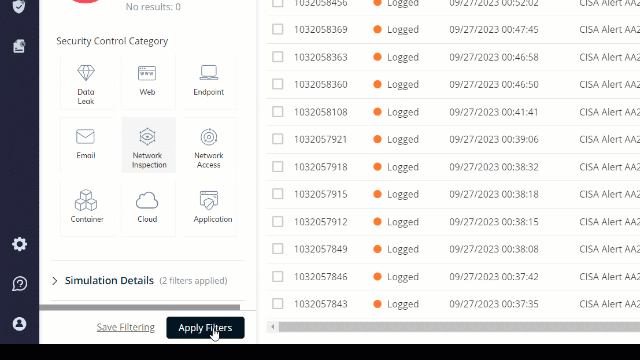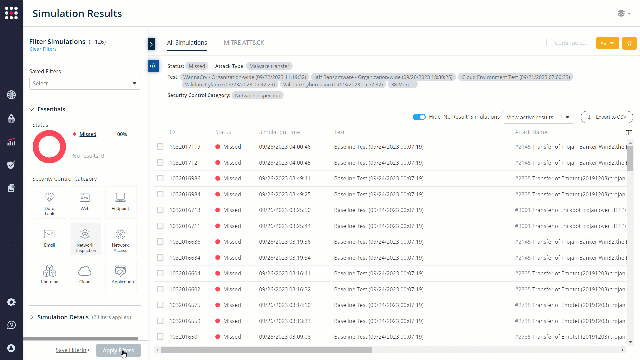
By filtering the security posture optimizer to specific cybersecurity measures, you can analyze specific data that interests you the most.
Choose security control category, and then attack type to analyze:
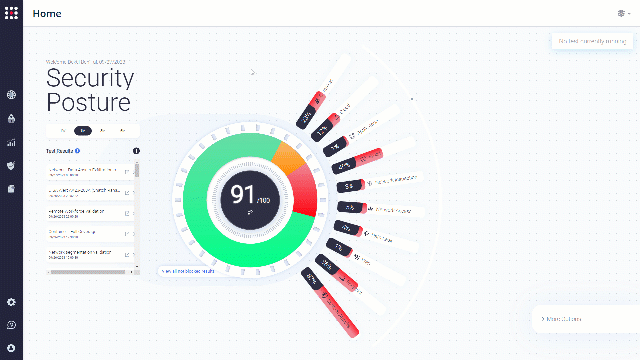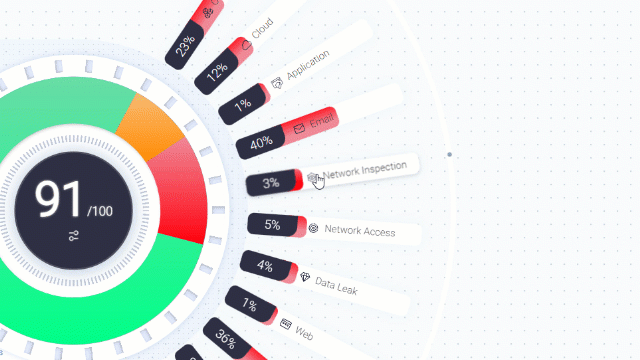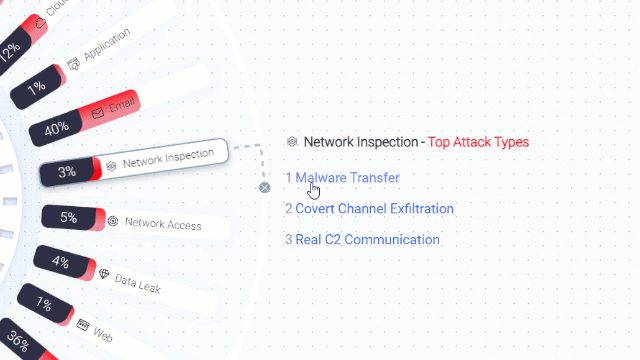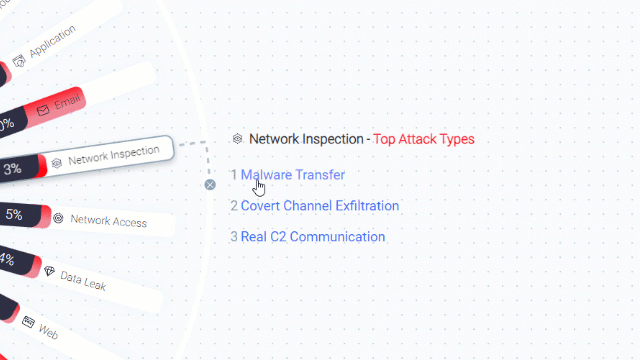
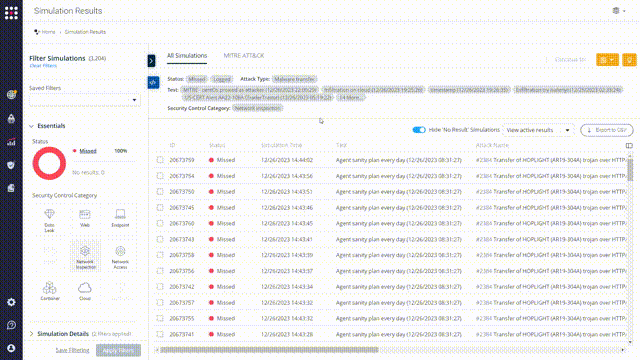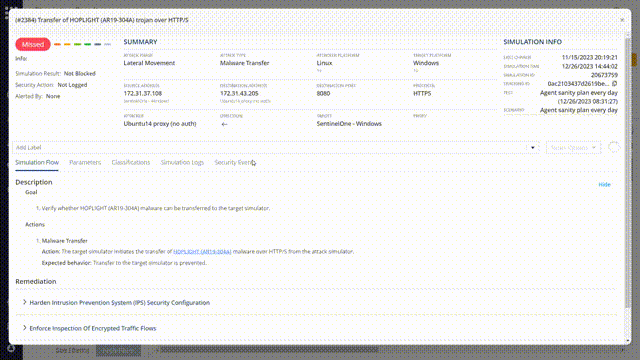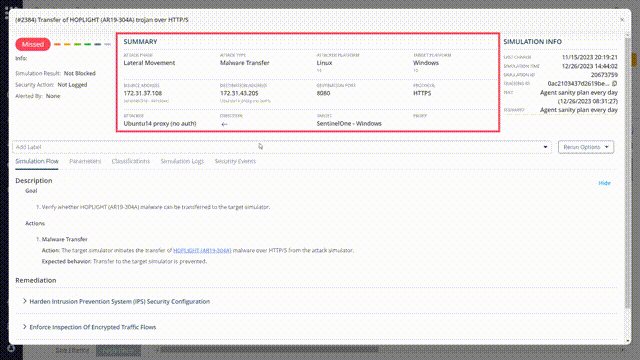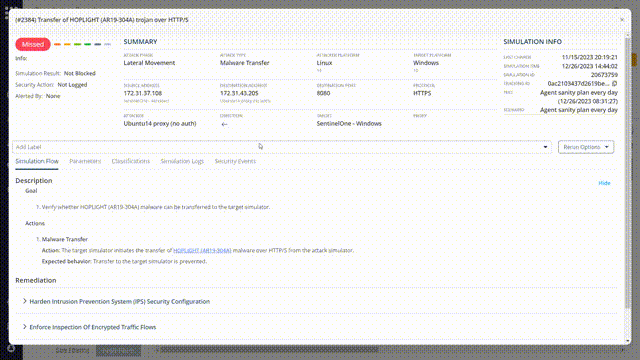
Filter the results to “Missed”:
Choose one of the missed attacks and investigate it. Look at the attack summary.
some key details can help you analyze the attack:
- Source address and destination address – can help you Identify the vulnerable “communication line”
- Destination port and protocol
- Direction – Will present the attack path between the two involved simulators
Investigate the attack using the bottom tabs:
Simulation Flow – Presents the attack flow, the expected result, and some recommendations for actions at the bottom.
Parameters – Presents the attack data and paths.
Classification – Presents the attack classification by MITRE, by industry, by attack groups, etc.
Simulation Logs – Allows a deep investigation of the attack steps and the export of a support file if needed. You can also rerun the simulation with PCAP to use network monitoring software.
Security Events – Lets you confirm or deny the hypothesis. Did your security controls detect the attack?
What Now?
Export the simulations to CSV and send it to your colleagues. the CSV file contains all the information needed to make sure that these attacks won’t be “missed next time.
MITRE ATT&CK Analysis
Use the MITRE board to discover your organization’s weaknesses. seeing your network vulnerabilities in a heatmap can you see the whole picture, bright and clear. This method especially fits MITRE oriented organizations.
Go to the MITRE ATT&CK board:
On the MITRE board, you can see a heatmap of your organization’s vulnerabilities. It’s easy to analyze it that way.
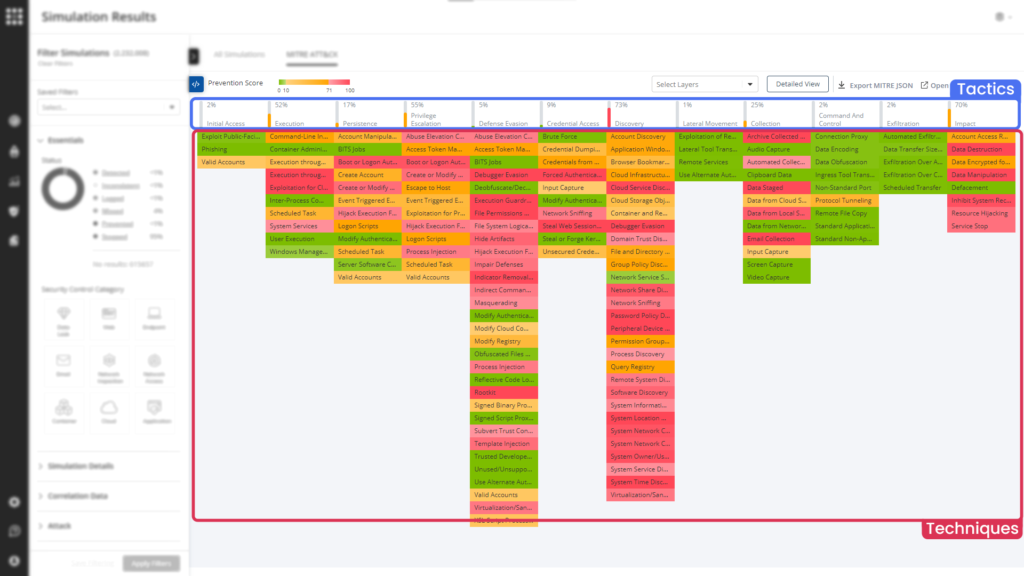
Choose a specific tactic or technique that you want to focus on. The simulation results will be filtered according to your choice.
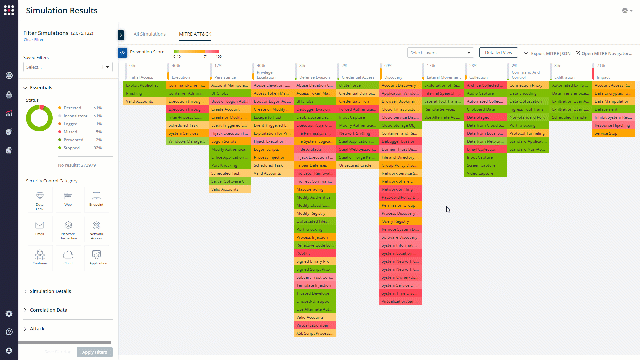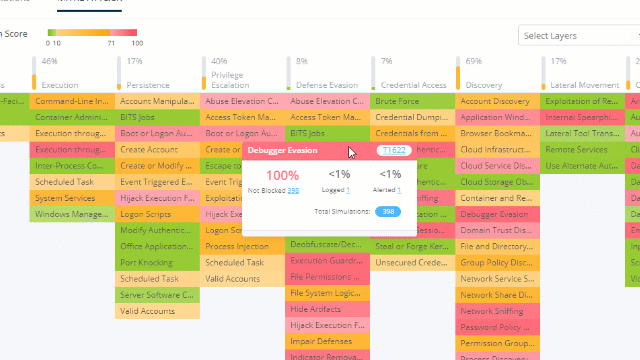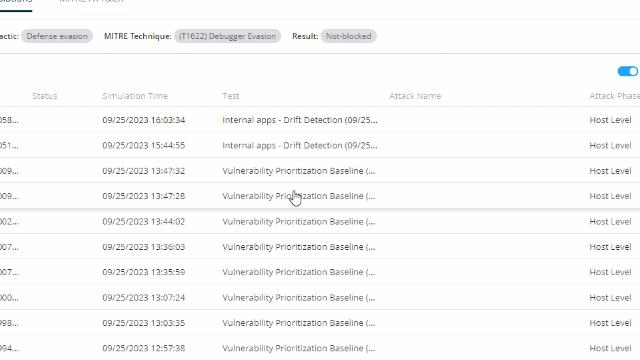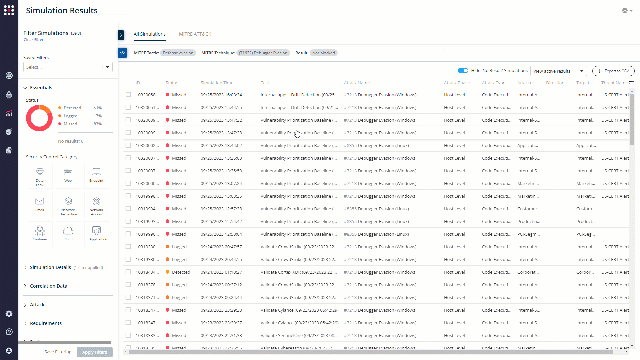
What Now?
Look for patterns. Ports or protocols that were exploited in a few simulations or more, a specific simulator that was attacked successfully many times, or a specific attack type that was 100% missed.
Breach Explorer Analysis
The breach explorer presents a “kill chain” of a cyber attack on your actual network, based on simulations and scenarios that you have run. Using this tool, you can efficiently discover your network’s weak points and understand where an attacker can reach.
Go to the Breach Explorer:
Choose a network component that you want to investigate:
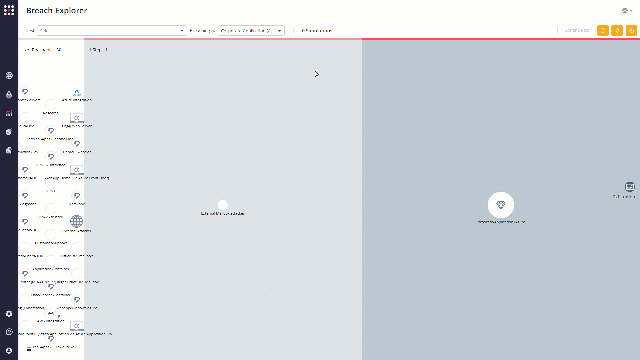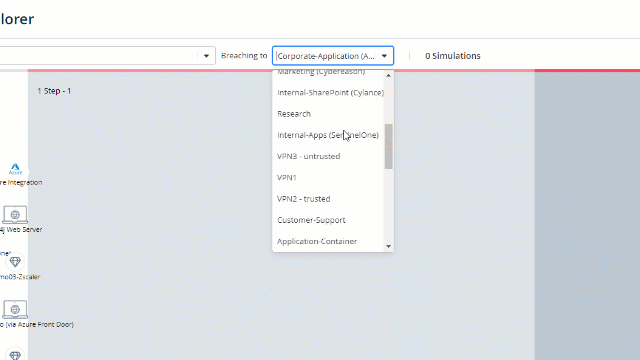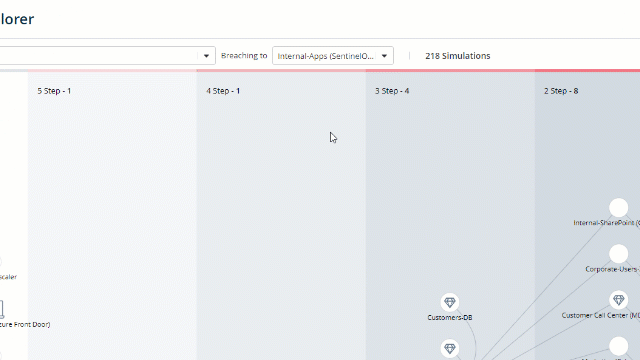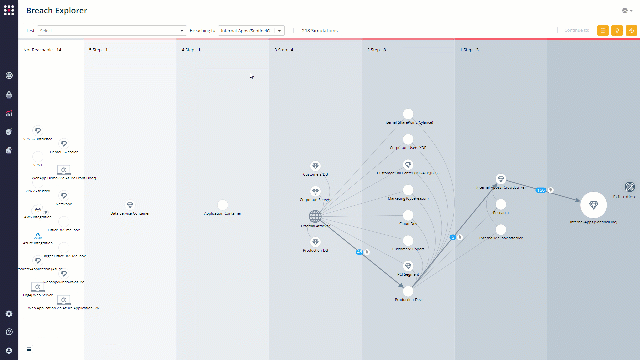
Look at the marked “kill chain”. These are the steps it took to the attack simulations to reach your chosen component, step-by-step.
Choose a chain to investigate. Click on the attack number and get a filtered simulation results screen.
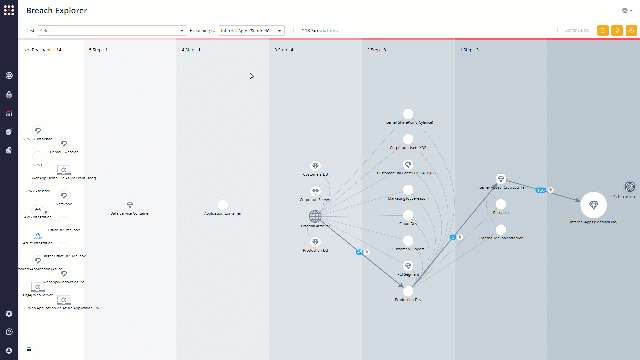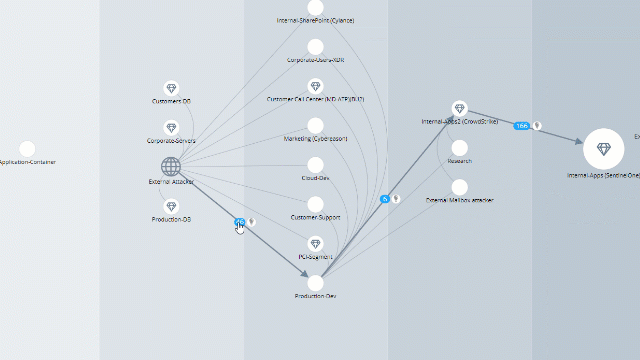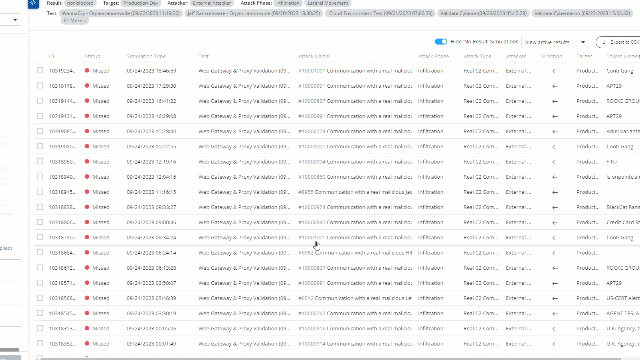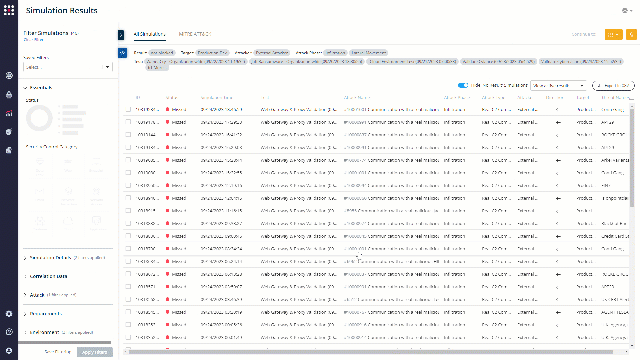
What Now?
Look for patterns. Ports or protocols that were exploited in a few simulations or more, a specific simulator that was attacked successfully many times, or a specific attack type that was 100% missed.
Lesson 2 -
Remediation Options
SafeBreach platform can provide useful insights that help in both behavioral and IOC-based mitigation processes.
IOC Remediation
Remediation based on Specific Indicators: Targets known and documented indicators of compromise (IOCs) such as file hashes, IP addresses, or malicious signatures.
Examples of IOC based remediation recommendations can be:
- Block known exfiltration methods and IP addresses
- Quarantine or delete files with known malware signatures
- Block known ransomware file extensions
To use this remediation method, open the insights page:
This page presents remediation insights based on all the tests you ran (or specific tests, per choice). The insight of the more severe issue will always appear on the top-left corner.
Choose an insight to focus and remediate and copy the query that works with your security control:
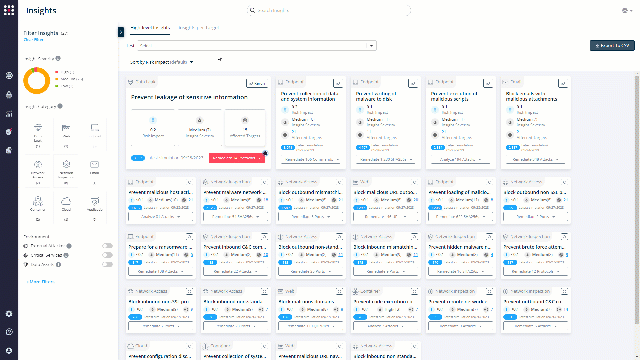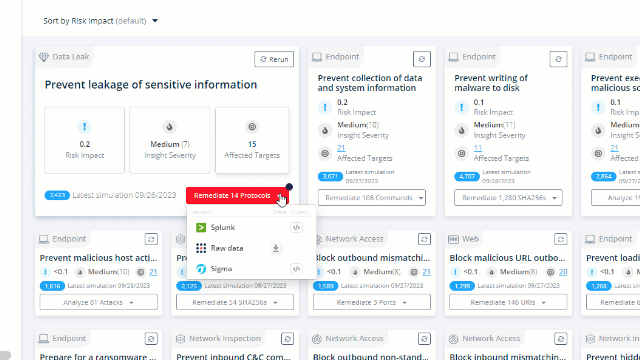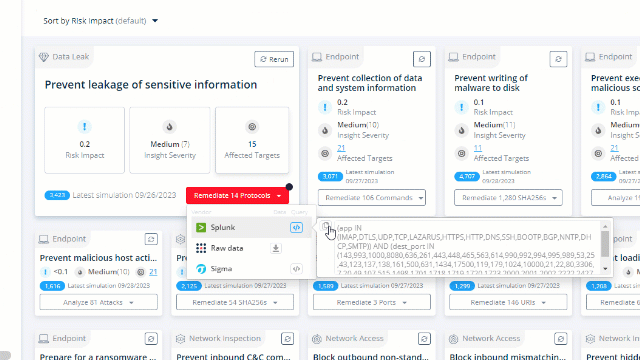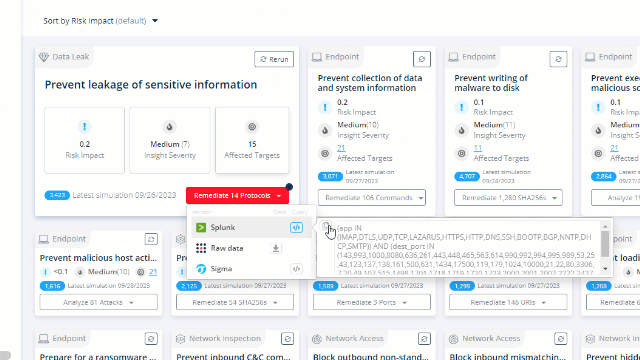
What Now?
Create a new policy or update your policy according to the insight you found. After changing the configuration, run a test that will test your new policy and look for for a change in the simulation result.
IOC Remediation - Demonstration Video
The video below demonstrates IOC remediation using insights from the insights panel, and IOC rules made in Crowdstrike.
Behavioral Remediation
Based on the identification of anomalous behavior. Focuses on identifying unusual or suspicious activities and patterns that might not be documented as IOCs.
Examples of behavioral remediation recommendations can be:
- Update your existing OS versions because of exploited vulnerabilities
- Isolate an affected endpoint or user account
- Analyze email traffic for patterns indicative of phishing, such as unexpected sender behavior or unusual URL click rates
- Monitor network traffic for signs of intrusion, such as unusual login attempts, lateral movement, or privilege escalation
Go to the Vulnerability Management page:
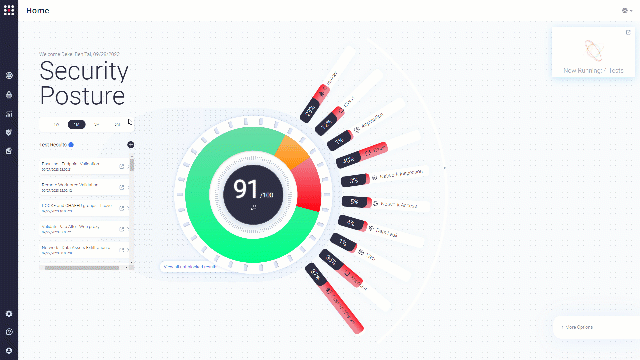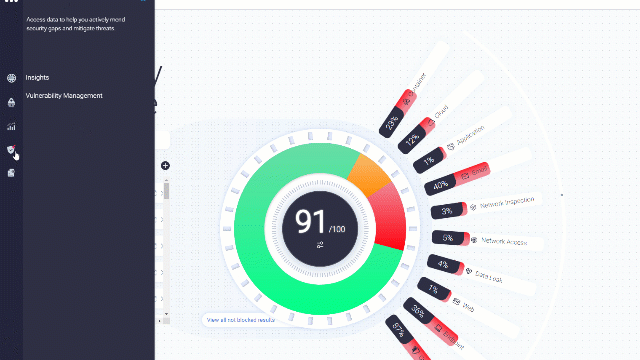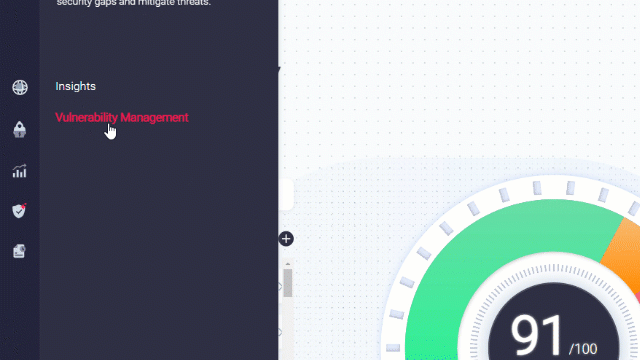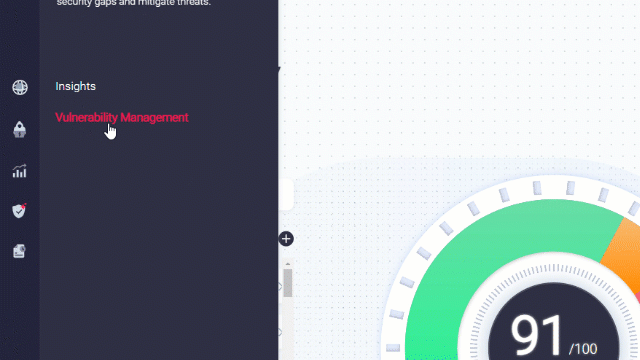
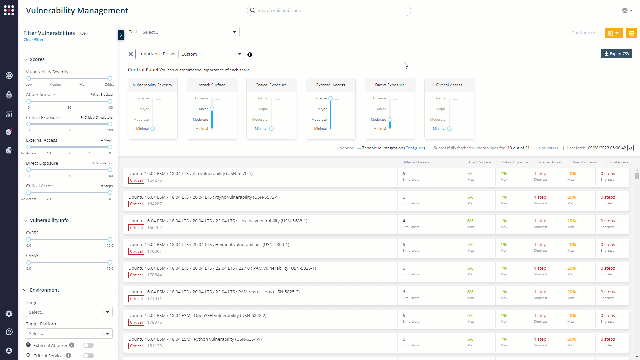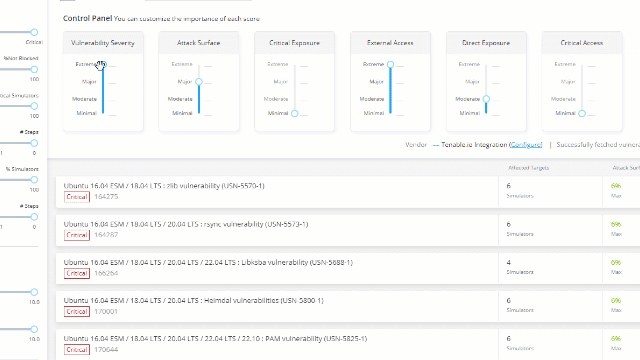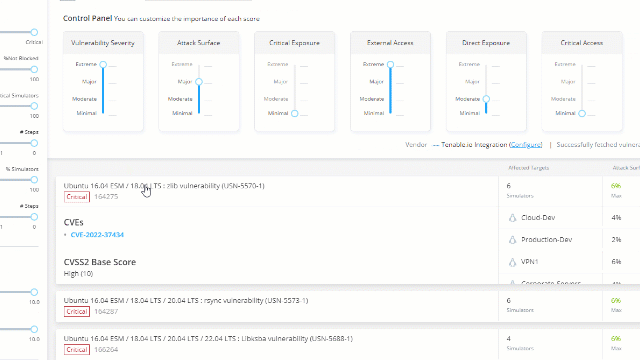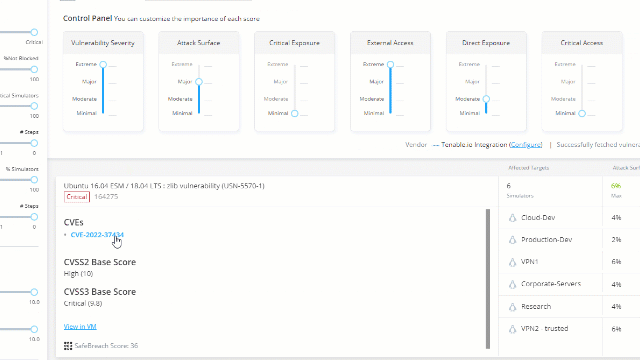
This screen presents remediation recommendations based on your existing VM vendor data. You can easily know which known vulnerabilities can affect your systems.
Order the list by severity and choose one of the vulnerabilities:
Behavioral Remediation - Demonstration Video
Another type of behavioral action that you can take is to prevent specific users from running specific commands.
Run attack scenarios that test command executions by impersonated users. Monitor which user was able to run commands, and prevent the execution of specific commands that can be abused by hackers.
The video below presents the whole remediation process. In this example, we will receive a list of commands that were able to run in a simulation. We will create a policy in Crowdstrike to block the users from running this command again.
Congratulations !
You have finished the course. Complete your Analysis & Remediation course journey with our final exam and become a certified SafeBreach Operator.